Via run-virtual.com.
Monday, August 31, 2009
T2'09 Challenge
0 commentsSorry for being a little late: the T2’09 challenge just started. Via the F-Secure weblog. Don’t be fooled by the fact that page already contains two entries (“Mr. Speed” and “Mr. Style”) in the top. From what I understand, these are to signal that two winners will be selected, one for speed and one for style.
The page also contains entries from past years for you to play with.
Careful with that axe^H^H^H static, Eugene!
0 comments An other instance from the “bugs which will bite you” series:
An other instance from the “bugs which will bite you” series:
public class TestStatic {
static class Foo {
static Foo instance = new Foo();
static String name = Foo.class.getName();
public Foo() {
System.err.println("Hello, my name is " + name);
}
}
public static void main(String[] args) {
System.err.println("Your name is what?\n"
+ "Your name is who?\n");
new Foo();
}
}
Can you spot the bug? Hint, here is the output:
Your name is what? Your name is who? Hello, my name is null Hello, my name is TestStatic$Foo
A final hint: here is what FindBugs reports on the third line: SI_INSTANCE_BEFORE_FINALS_ASSIGNED
Yet an other reason to reduce your FindBugs count to zero before releasing software!
Picture taken from helena.40proof's photostream with permission.
Saturday, August 29, 2009
Freakonomics review
0 commentsI know, I know, I'm quite late to the game (Freakonomics was first published in 2005), but I still feel that this book deserves a review.
What I like about it the most, is the fact that it tries to teach critical thinking, a thing which is lacking these days. The book provides vivid and easy to read descriptions of investigative stories, similar to detective/murder-mystery books, about how seemingly distant events relate to one-another. Each chapter stands on its own and can be read-trough in a short amount of time. Where necessary, the book provides high-level description of the statistical terms (like regression-analysis), without giving the impression of "talking down".
My favorite quote from the book is actually not from the book authors, but non-the-less I find it very fitting (and I'm sure that the authors agree with me, since they included it in the book :-)):
"We Associate truth with convenience," he wrote, "with what closely accords with self-interest and personal well-being or promises best to avoid awkward effort or unwelcome dislocation of life. We also find highly acceptable what contributes the most to self-esteem." Economic and social behaviors, Galbraith continued, "are complex, and to comprehend their character is mentally tiring. Therefore we adhere, as though to a raft, to those ideas which represent our understanding."
I consider this book one worth reading. The only negative was that I got the "extended" version (which is not the one I link to) and I found that the "extension" was just some rehashing of the content from the book and from their blog. So get the real thing.
PS. Wikipedia says (so it must be true :-p) that a sequel is coming. I'm looking forward to it! Even if it will be half of the quality of the original (as sequels usually are), it should still be a great read!
Full disclosure: the links include my Amazon Affiliate ID.
Friday, August 28, 2009
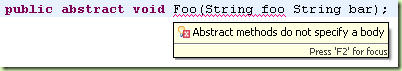
Spot the error
0 commentsC++ compilers are notorious for giving error messages which point you in the wrong direction. However even simpler languages can have issues. Can you spot the real problem with the java code below?
There is a comma missing between the parameters! Nice, ey? (To be fair, on the sidebar Eclipse shows two errors, one of which correctly identifies the problem, but I still scratched by head for a few moments).
Thursday, August 27, 2009
Perl is everywhere!
0 commentsSomething which is not appreciated enough IMHO is just how much of the interwebs runs on Perl: for example Frozen Bubble is written in Perl. Also, from some error messages I’ve got the impression Yahoo Pipes uses (is written in?) Perl.
And just before you accuse me of being a Perl fanboy (which I am BTW :-p), here is a fascinating document: Far More Than Everything You've Ever Wanted to Know about.
Youtube gadget generator
0 commentsSome time ago I posted about how the Google Gadget code for Youtube seems to be borked up. Now it seems that they completely removed the option from the YouTube pages, for whatever reason, but the old code still seems functional. So below you can find a small Javascript which generates the equivalent code for a given Youtube user (if you are reading this in an RSS reader, you need to click trough to the post page, since chances are that the reader stripped out the JS for security reasons).
Of course this is an unofficial and unsupported solution, so it might break at any time and without warning!
:
Advanced Windows Debugging review
0 comments Until recently I didn’t do kernel debugging, but recently I’ve toyed around with some code which executes before the the process is in a state which is agreeable for user-mode debuggers. So I borrowed this book from one of my friends (thanks D!) and read trough it.
Until recently I didn’t do kernel debugging, but recently I’ve toyed around with some code which executes before the the process is in a state which is agreeable for user-mode debuggers. So I borrowed this book from one of my friends (thanks D!) and read trough it.
To get the bad stuff straight out of the way:
- The authors define a very wide scope for the book in the introduction (something along the lines of “everyone should read it” – of course I’m paraphrasing). There is stark contrast however between this statement and the level of knowledge required to be able to understand the book, knowledge mostly isn’t covered in the book
- A large part of the book is monospaced textual content. They don’t use a typeface however in which you can easily differentiate between the letter l and the digit 1 (like Monaco), which makes many of the examples ambiguous
- The chapters have a certain feel of disorganization to them in my opinion, and frequently they seem to be more of a “tips & tricks” collection than complete whole. I assume that a large reason for this is the fact that the WinDBG commands evolved over time, so there isn’t a simple logic which can “decode” all of them (similar to the MS-DOS/MS Windows batch language). Still, a summary of the commands (in cheat-sheet fashion) would have been nice.
One positive aspect of the book is its low error rate. In fact I’ve seen only one error in the whole book (there might have been more, but not many more): a drawing shows the end of the SEH chain as being 0x00000000, while in fact it is 0xFFFFFFFF (the correct value is used however in the text). An other positive aspect is the thoroughness: after reading trough all off ~750 pages, you will get a very good idea about the capabilities of WinDBG and other related tools.
So would I recommend reading this book? If you want to use WinDBG (or other debuggers from the Windows Debugging Tools) yes, but only after reading at least the Windows Internals and an assembly book (I've heard that Art of Assembly would be good, although I've didn't read it myself). It should have a warning sticker: for hard-core enthusiast only.
Full disclosure: the links in the post contain my Amazon Affiliate ID.
Wednesday, August 26, 2009
If you can't access Windows shares...
1 commentsA small Windows tip: if your computer is part of a domain and all of the sudden you can't access resources over the network (like shares, printers, etc), try changing your password.
I observed this in several networks, and although I'm not entirely sure about the reason - I suspect that it has something to do with the password expiration policy (even though the password seem to work when logging into the given system - even after a cold boot) - this workaround always seemed to work.
Update: Here is the discussion on serverfault about the problem. There were some good suggestions by Nico, but unfortunately no final solution was found as of now.
Picture taken from gemsling's photostream with permission.
delicious/cdman83
0 comments| Posted: 16 Aug 2009 08:37 AM PDT An open-source CISCO simulator. All you need are some IOS images :-). Via http://synjunkie.blogspot.com/2009/08/bit-of-change-yet-another-update.html |
| QuirksBlog: When to read out the end time in browser speed tests Posted: 17 Aug 2009 07:00 AM PDT Know what you are measuring. For an other example see: https://mailman.cs.umd.edu/pipermail/findbugs-discuss/2009-August/002911.html |
| Posted: 17 Aug 2009 01:34 AM PDT An extraterrestrial race forced to live in slum-like conditions on Earth suddenly find a kindred spirit in a government agent that is exposed to their biotechnology |
| “das Mädchen” – why is it grammatically neutral? Posted: 18 Aug 2009 02:47 AM PDT |
| Colour Overload with IE8 Tab Grouping Posted: 18 Aug 2009 02:46 AM PDT How tab coloring in IE can lead to mistaking it for EV certificates. |
| SSL Labs - Projects / Public SSL Server Database - SSL Server Test Posted: 18 Aug 2009 02:45 AM PDT An other SSL tester. |
| N.E.R.D.: Stream your Linux/Windows/Mac Desktop as video using VLC Posted: 21 Aug 2009 02:59 AM PDT |
| BBIE - Bart's Boot Image Extractor Posted: 21 Aug 2009 01:43 AM PDT |
| Posted: 20 Aug 2009 11:11 PM PDT Why the screensaver won't start and how to prevent it from starting programatically? |
| Posted: 22 Aug 2009 03:55 AM PDT |
| Nao and Zen: Security Koans for Everybody Posted: 23 Aug 2009 12:34 AM PDT |
| Roundtable: High Frequency Trading Posted: 24 Aug 2009 01:26 AM PDT Via ZeroHedge (http://www.zerohedge.com/) |
Friday, August 21, 2009
The myth of the cognitive quantum jumps
2 commentsUpdate: see this presentation given by Scott Berkun at Google, which which explains my points much more eloquently.
 Very often media (and I’m using the word “media” here in its most comprehensive way – including things like blogs, Slashdot, etc) tells us the story of some uber-hyper-mega-cool new-unseen-until-now method of performing X. This leads many people to believe that progress is done in “quantum leaps” – ie. there are no intermediate steps between point A (where we are now) and point B (where we can get using this new discovery). As a side-effect, it also makes people think that all they have to do is to come up with a “big idea”.
Very often media (and I’m using the word “media” here in its most comprehensive way – including things like blogs, Slashdot, etc) tells us the story of some uber-hyper-mega-cool new-unseen-until-now method of performing X. This leads many people to believe that progress is done in “quantum leaps” – ie. there are no intermediate steps between point A (where we are now) and point B (where we can get using this new discovery). As a side-effect, it also makes people think that all they have to do is to come up with a “big idea”.
This is utter nonsense and I would like to ask everybody to stop propagating this myth! (Of course I know that it is wishful thinking on my part to think that this blogpost would have a large impact on humanity, but hey, at least I’ve vented my frustration, and if just one person is convinced, I’m happy).
There are at least two factors which mislead people into this fallacy: first, the lack of knowledge of the reader in a particular field. So, there is no chance for the reader to evaluate what works the current one is based upon, unless this is explicitly mentioned by the author. And here is the second problem: our tendency to over-emphasize (either intentionally or unintentionally) our contribution.
Also, there are a lot of both empirical and scientific evidence for the fact that progress is not as simple as coming up with one great-idea. The quote from Thomas Edison (“Genius is 1 percent inspiration and 99 percent perspiration”) illustrates this. A more scientific study comes from Malcolm Gladwell, who says that you need about 10 000 hours (about ten years) of deliberate practice to become great in a given field.
One example which comes to mind from the field of malware-research is the case of the Storm worm. When it “appeared”, there was a big media frenzy around it, fueled mainly by the AV companies. What nobody mentioned (because it would have broken the myth of “new, ultra-dangerous malware materializing from nowhere”) is that “Storm” is in fact the “normal” evolution of a much older malware family detected by many as “Tibs”. If one would to place the samples on a timeline and study them in the order as they appeared, one could clearly see how the different methods (like using a simple encryption layer over UPX, using different API calls to thwart emulators, using MMX/SSE instructions, using the return values of the API calls in the decoding process, etc) appeared and evolved. In fact “Tibs” and “Storm” are very clearly the work of the same group of people, and not something new as the reports would like you to believe.
No quantum leaps (except in theoretical physics :-))!
Picture taken from renrut's photostream with permission.
Wednesday, August 19, 2009
Educational investment resource
0 comments Yesterday I wrote about FORA.tv, and today I have an free other online educational resource for those who are interested for a reason or other in the world of finance / investment: the MarketPlace Whiteboard (found it via zero hedge).
Yesterday I wrote about FORA.tv, and today I have an free other online educational resource for those who are interested for a reason or other in the world of finance / investment: the MarketPlace Whiteboard (found it via zero hedge).
Here senior editor Paddy Hirsch explains with the help of a whiteboard (hence the name) and some simple and easy to understand metaphors all kind of concepts from high-frequency trading to credit default swaps. If you are a newcomer to the world of finance / investment, this is a great resource which will make it possible for you to understand more and more of the concepts and the discussion which is going on around them.
Picture of the Tokyo Stock Exchange – taken from Stéfan's photostream with permission.
Tuesday, August 18, 2009
A new security provider
0 commentsI found out about Dasient via the presentation they did at Google (which you can see embedded below). Their angle seems to be (although this probably will change – them being a young company) that: we check your rating at Google / McAfee / Symantec and if they say that you are bad, we will find the pages which are bad and “fix” them for you (by removing the malicious code).
What bothers me:
- The blacklist approach – this means that there will be a lag before new attacks are detected
- Relying on third-party service (like the Google Safe Browsing API, McAfee SiteAdvisor, etc). While the Google Safe Browsing API has an explicit TOS stating that you can use it (under certain circumstances of course), the situation with McAfee and Symantec is not as clear-cut. Does Dasient have a contract with them or are they just scraping their websites? What if McAfee / Symantec decides that enough is enough and blocks them or even worse, sues them? Also, relying on these services means further delay in detecting the infected sites (because they must wait until these providers detect the infection)
- Their touted “dynamic filtering” technology seems to be over engineered for me. It also (as far as I understand) can’t handle situations like “the request is directed to a different machine” or “the machine is rootkitted and the malicious code is added on-the-fly”, both of these being situations which occurred in the real world (the first with CN CERT and the second with a bunch of compromised Linux machines)
- Also, I fear that because this filtering masks the problem (much like a WAF does), it will encourage people to be complacent about fixing the root of the problem (“so what if we get compromised twice a day due to weak passwords? we just click the checkbox!”)
- Finally, the prices seem a little steep to me (starting from ~10 USD a month and going over ~ 50 USD per month)
All in all it doesn’t seem to me to be worth 2M USD (which they claim to have in funding)...
Know thy (cryptographic) functions
0 commentsMore than I year ago I mentioned that VNC uses only the first 8 characters of the password to validate it. Today I found an other situation where this happens: the crypt function (to be fair, the glibc version of it has the option of using all the characters, but still we have the issue of legacy code). From the manpage (emphasis added):
By taking the lowest 7 bits of each of the first eight characters of the key, a 56-bit key is obtained.
Other software can also be exposed indirectly to this issue, for example PHP contains a binding to crypt which can use the old (insecure) way for generating hashes.
In conclusion:
- good - train yourself and your peers / subordinates in security issues
- better - limit the security code to a small library and validate it thoroughly
- best - use a third-party, independently validate, high-level library which uses industry standard functions
Windows 7 OOP overdrive
1 commentsCredit goes to a good friend of mine for this (who doesn’t have a website or twitter account, so I can’t link to him :-p). Here is a (partial) list of DLL’s imported by the Windows 7 version of kernel32:
API-MS-Win-Core-RtlSupport-L1-1-0.dll
API-MS-Win-Core-ProcessThreads-L1-1-0.dll
API-MS-Win-Core-Heap-L1-1-0.dll
API-MS-Win-Core-Memory-L1-1-0.dll
API-MS-Win-Core-Handle-L1-1-0.dll
API-MS-Win-Core-Synch-L1-1-0.dll
API-MS-Win-Core-File-L1-1-0.dll
API-MS-Win-Core-IO-L1-1-0.dll
API-MS-Win-Core-ThreadPool-L1-1-0.dll
API-MS-Win-Core-LibraryLoader-L1-1-0.dll
API-MS-Win-Core-NamedPipe-L1-1-0.dll
API-MS-Win-Core-Misc-L1-1-0.dll
API-MS-Win-Core-SysInfo-L1-1-0.dll
API-MS-Win-Core-Localization-L1-1-0.dll
API-MS-Win-Core-ProcessEnvironment-L1-1-0.dll
API-MS-Win-Core-String-L1-1-0.dll
API-MS-Win-Core-Debug-L1-1-0.dll
API-MS-Win-Core-ErrorHandling-L1-1-0.dll
API-MS-Win-Core-Fibers-L1-1-0.dll
API-MS-Win-Core-Util-L1-1-0.dll
API-MS-Win-Core-Profile-L1-1-0.dll
API-MS-Win-Security-Base-L1-1-0.dll
I guess somebody found an OOP book and started applying the “single responsibility principle” to kernel32 :-). What does this mean to you? If you are an end-user, nothing. If you are a RE or a low level programmer, take care because many functions from kernel32.dll are now forwarded into these DLLs instead of being directly implemented.
Update: here is a little more detailed post on the Avert Labs / McAfee blog.
FORA.tv
0 comments I discovered FORA.tv just recently, but I’m already a huge fan. If you like TV channels like Discovery or National Geographic, you will certainly find something of interest here.
I discovered FORA.tv just recently, but I’m already a huge fan. If you like TV channels like Discovery or National Geographic, you will certainly find something of interest here.
What’s great:
- it’s free with very little and unobtrusive advertisement
- the programs are professionally recorded / postprocessed (no volume-to-low-to-hear problems here)
- link to individual parts of the program
- a lot of supporting materials (like transcripts) and even audio and video downloads!
- possibility to embed the videos on other sites like blogs
- recommendations (“related programs”) which are pretty much spot-on (or maybe I’m just a video-junky :-))
Much of the functionality is available to non-registered users, and if you want to register, it is a quick and painless. A minor problem is that the links in their RSS feeds is sometimes wrong, but this is rare and looks like user error, and as such it is rather easy to guess the correct URL (like putting one “r” instead of two).
Just to get you started, here are two episodes about Adam Savage and Jamie Hyneman of Mythbusters fame:
You can also check out their blog for some behind-the-scenes look.
Enjoy!
Disclaimer: I have no other relationship with FORA.tv, other than being a satisfied and enthusiastic user.
Creating a closed standard
0 commentsAfter reading on Graham Cluley's blog that the IEEE came up with a new standard [PDF] for malware interchange, I had to check it out immediately. As always, being a cranky old man, I found several problems with the proposed standard:
- Even though the presentation has a section abou "Re-Inventing the Wheel", it fails to mention that such sample exchange has been going on for at least a decade at this point between participants of the AV industry
- It fails to address the issue which traditionally concerned the people the most: who should the samples be shared with?
- The specification is tied strictly to proprietary products, where at least comparable (if not better) open products exists, the adopting of which would ensure that these files can be easily processed on any platform: RAR and PGP. While they both are excellent products, their selection also means that there is a minimal license fee for anybody interested in producing such archives. Also, certain encryption schemes of PGP are not implemented in GnuPG because of patent concerns, but the document doesn't mention this. A much better option would have been to go with 7-zip and GnuPG for example (and explicitly stating that patent encumbered encryption algorithms won't be used).
- The strictly defined attributes (like md5, sha1, sha256) can be easily recalculated at the receiving end. You might argue that they provide an integrity check, however the presentation explicitly states that the archive provides this function - "RAR-archived (for integrity checking)"
- Some of the definitions are lacking in detail - for example they introduce a "classification" tag, but it doesn't seem to include timestamp / engine version / signature version information. Without these, in todays dynamic world, the information is not very useful.
- Many of the fields are "free-form", meaning that no complete automatic parsing can be done.
The conclusion? This format doesn't bring anything new to the table and is (as it stands) just a poorly thought out waste of time.
Monday, August 17, 2009
wpdesigner.com review
0 commentswpdesigner.com is an other blog / resource targeted at WordPress users. It has the usual categories, like webhosting, themes, tips, tutorials and so on. I especially liked the “How to Get Help for WordPress Problems” section, mainly because it starts with “Search Before You Ask” (but the other tips it gives are also good). The free wordpress themes section is also good. Not only does it show snapshot for each theme, but it also shows detailed information like license and for many of them it contains a “liked/disliked” list. While you might not agree with everything written in these reviews, it gives a good starting point for people interested in checking out a theme.
What I disliked: the front-page theme is too minimalistic in my opinion and misses the opportunity to feature more in-depth content from the blog. You have to go and dig yourself to see what things you can find (you can see the announcement of the new theme here, and a screenshot of the previous theme – which seems much nicer – here). Also, from the contact page it seems that wpdesigner just changed ownership, and it is not clear in what direction the new owner will take it (or who the new owner is for that matter).
If you are a WordPress user, browse around – you might find something interesting.
Full disclosure: this is a paid review from ReviewMe. Under the terms of the understanding I was not obligated to skew my viewpoint in any way (ie. only post positive facts).
Those who know, do it
0 comments There is an old joke, which I might have referenced in the past (my memory is almost non-existing :-P), which goes something like this:
There is an old joke, which I might have referenced in the past (my memory is almost non-existing :-P), which goes something like this:
Those who know how to do X, do it. Those who don’t, teach it. Those who can’t even teach it, supervise it.
I assume that journalists come in somewhere in the second or third category. Take the following article from Ars Technica for example: Symantec, 11 others, fail Virus Bulletin's August 2009 test (Updated). Quote (emphasis added):
Microsoft's success with its Forefront product is promising not only for business users, but for consumers as well, given that the upcoming Microsoft Security Essentials product is closely tied to it.
Now we go over to the Microsoft Forefront site, the whitepaper section in the first one (The Multiple Scan Engine Advantage and Best Practices for Optimal Security and Performance) we have the following (again emphasis added):
Forefront Security for Exchange Server and Forefront Security for SharePoint each ship with multiple scan engines, and customers can use up to five scanning engines simultaneously.
The performance of Forefront Security in tests (or in the real world for that matter) has almost zero relevance for the performance of Morro (aka. Microsoft Security Essentials). Coincidentally I think that both are good products, but this is not because they share code/signatures.
An other example is the following one: Computer viruses slow African expansion (found it via the Sunbelt Blog). To be fair, in this case the reporter only repeats the insanity “Tariq Khokhar, the chief development officer of Aptivate, a non-governmental organisation that focuses on IT” says, but would he be more informed, he could have asked some pointed questions to debunk some of the things said. For example:
Without special pricing, poor countries are forced to rely on free antivirus products, such as AVG. "Writing antivirus software is a fairly brain-intensive task, and AVG just don't have the resources," Khokhar says. "It's not to say something's not better than nothing, but ultimately, the viruses that are going to cause real damage are going to get through."
First, in the long run (meaning a year in this example) AVG is just as effective as any other product (as would be MS Security Essentials, despite of what some say). Second of all, you just can’t rely on one “magic pixie-dust solution” (eg. AV) to solve the problems. You need a layered approach, for example for the ISP to block known malicious sites. Third of all, you need user education. He (I assume it is a he) works for an NGO, so go create some education programs for new computer users. Also, there are a lot of dangers out there (like 419 scams), which have nothing to do with malware, but can be just as (or even more) devastating as a malware attack. Please, people, go inform yourself!
Picture taken from fsse8info's photostream with permission.
A couple of challenges
0 commentsThe Google code-jam. Algorithmic, ACM-like programming challenge (don't forget about UVa if you want to get some warmup).
A "find the vulnerability" type contest from Immunity.
A Javascript compression contest - this is not an "official" contest (in the sense that there are no prizes and no very strict rules), but more of a "one-upmanship". Still interesting though.
Update: I almost missed this one: Network Forensics Puzzle Contest.
delicious/cdman83
0 comments| PostgreSQL Experts Inc. - Presentations and Documents Posted: 14 Aug 2009 05:09 AM PDT Some very interesting presentations, related mostly to PostgreSQL, but there are more generic ones also. |
| Common gotchas when writing your own p/invoke Posted: 14 Aug 2009 12:16 AM PDT |
| Social Media Policy and Employee Guidance Posted: 12 Aug 2009 10:05 PM PDT |
| Cross Compare of PostgreSQL 8.4, SQL Server 2008, MySQL 5.1 Posted: 12 Aug 2009 10:01 PM PDT |
| LockHunter is a free 64/32 bit tool to delete files blocked by any processes Posted: 12 Aug 2009 03:17 AM PDT Similar to http://camtech2000.net/Pages/UnlockMe.htm / http://ccollomb.free.fr/unlocker/ Via http://delicious.com/absoblogginlutely#2009-08-11 |
| Free Websites Performance, Availability, Traffic Monitoring Posted: 11 Aug 2009 10:52 PM PDT Availability monitoring with a free basic plan. Sounds nice! Via http://blogs.technet.com/rhalbheer/archive/2009/08/11/monitoring-a-key-activity-to-a-trustworthy-infrastructure.aspx |
| Posted: 11 Aug 2009 07:44 AM PDT Nice "HijackThis" style of utility. A nice add-on is the filtering by risk and find feature. |
| ezds.com : Self Deleting Executable by Gary Nebbett Posted: 11 Aug 2009 07:01 AM PDT A very cool return-to-glibc style method for self-deleting executables. |
| Sun VirtualBox® Documentation - Responding to guest IDE flush requests Posted: 11 Aug 2009 06:58 AM PDT Virtualbox doesn't flush the harddisk when the guest requests it by default. This can lead to corruption of the guest! Via http://openquery.com/blog/host-flush |
| Posted: 11 Aug 2009 06:56 AM PDT Interesting little online game |
| NNDB Mapper: Tracking the entire world Posted: 11 Aug 2009 04:48 AM PDT Via ZeroHedge: http://www.zerohedge.com/article/fun-nodes |
| utrace - locate IP addresses and domainnames Posted: 11 Aug 2009 12:45 AM PDT Interesting IP geolocation tool, with an API! Found it via http://blog.rootshell.be/2009/08/10/easy-geolocalization-of-ip-addresses/ |
Thursday, August 13, 2009
The Yellow Smiley Face
0 commentsThe short film below is from the Portable Film Festival site. It is a very good one and worth watching, even if you don’t speak Romanian (it is subtitled in English). It is a piece of life captured in a masterful way (I’ve uploaded it to blip.tv because the Portable Film Festival site seems to be a little flaky – hopefully because they have huge traffic :-)).
Incidentally, this brings to mind an other thought: why Microsoft shoot themselves in the foot with the interface changes in Windows Vista / 7 and Office 2007 / 2010? Because, logical and intuitive as they might be, the wast majority of people in Romania (and I expect this to be true of most other non-English speaking countries) do not use the localized versions of computer software, even though they don’t speak English! What this means is that their knowledge level is exactly like it is depicted in the shortfilm: “I have to click the forth item in the third menu”. This means that any extensive overhaul of the GUI (like the one seen in MS Office 2007 and which are predicted for MS Office 2010) essentially wipes out all the knowledge these people (who represent 99% of the userbase in countries like Romania).
This means that these people will refuse to upgrade and will clinch even harder to Windows XP / Office 2003 than the companies in the US who don’t upgrade for “business reasons”. It also means that software packages like OpenOffice.org (or AbiWord) have a big chance to position themselves as a replacement to MS Office: they cost less and they have a familiar interface.
PS. Dear reader, if you are from outside of the USA, I would be interested to hear from you: is the situation similar in your country too?
Friday, August 07, 2009
Open letter to PhishTank
4 comments Dear PhishTank!
Dear PhishTank!
I’m writing this letter / blog post because I couldn’t find any contact addresses on your site or a user forum to voice my concern.
The idea of crowd-sourcing the phish detection great because it lets a human make judgment about threats directed at humans (which is much easier than developing and maintaining an AI system :-)). I first joined PhishTank when I received some phising emails and I wanted to “do the right thing”. However after a couple of days of “verifying” phishes I was filled with an overwhelming sense of futility because of several reasons:
- The last blogpost on the phishtank blog is from October 2008 (more than 8 moths ago at this moment!). And the comments are closed. Just an other way you can’t give feedback
- The rules behind the functioning of the site are somewhat mysterious. Sometimes when I’m the first to vote on a site, it goes to 100% in the “is a phish” / “is not a phish” category, other times it remains at zero (as if my vote wasn’t counted)
- Every time I vote it says “more votes are needed to verify this site”. Does this mean that even though I’ve casted hundreds of votes, I didn’t verify a single site as being a phish? Talk about futility...
- Many phising sites are taken down quite quickly, so it is not uncommon to only see a “this site has been taken down” message when you want to verify a URL. However there is no way (that I’ve found) to say “this might have been a phish (based on the URL for example), but it seems to be taken down”
- There are no statistics shown about the number of submissions versus the number of verified sites. It would be nice to see if we (the volunteers) can handle the load or if we need more volunteers
- It would be nice to offer advice on setting up a safe environment for verifying phishes. Something like: a separate instance of Firefox with Javascript entirely disabled and perhaps Tor.
- An other idea would be (if the amount of submitted URLs is far greater than the daily verified ones) to prioritize those URLs which are not yet in the Google Safe-Browsing database. This way PhishTank could offer a very good complement to the Google data-set.
If somebody from PhishTank reads this, please fix as many of the issues as possible! It is very sad to see a good idea being hindered by technical problems. BTW, I would be happy to help out (I have considerable experience in some key areas: PHP / MySQL / computer security).
Picture taken Sandy Austin's photostream with permission.
Some fun timewasters :-)
0 commentsFound this one via h-i-r.net:
And the following one is from friends (these are in German, but many of them can be enjoyed even if you don't know the language):
Some of the highlights from both of the channels:
Virtually Hosted SSL – almost there
2 comments Virtual hosting (hosting multiple sites on the same IP address) became possible with HTTP/1.1 because it declares the “Host” header, which specifies which one of the (possibly) multiple sites hosted on the same IP address you would like to reach (a small side-effect is that when you use the IP address of a site, you might get a different site, since the web-server doesn’t know which one to pick).
Virtual hosting (hosting multiple sites on the same IP address) became possible with HTTP/1.1 because it declares the “Host” header, which specifies which one of the (possibly) multiple sites hosted on the same IP address you would like to reach (a small side-effect is that when you use the IP address of a site, you might get a different site, since the web-server doesn’t know which one to pick).
However this wasn’t possible with SSL, because the certificate was sent before the headers and a certificate is specific for a site (at least the run-of-the mill ones), and the webserver didn’t know which certificate to pick. When I’ve heard on the SANS Daily Stormcast that the newest version of Apache included a way to do this, I was enthusiastic and intrigued at the same time, so I went looking and found the following thing:
- It is done by doing the initial communication in plaintext and then “upgrading” to TLS. I wonder just how much is in plaintext? (see the What’s new document – the mod_ssl section specifically)
- The official RFC for this is RFC 2817. The RFC specifies both methods for upgrading – before and after the actual request – so the devil will be in the
detailsimplementation - There is no browser support for this as of this moment, so it is pretty much useless (until IE + IIS starts supporting it is pretty much a cool option). But at least we have a reference implementation
Bonus article: The First Few Milliseconds of an HTTPS Connection
Picture taken from AMagill's photostream with permission.
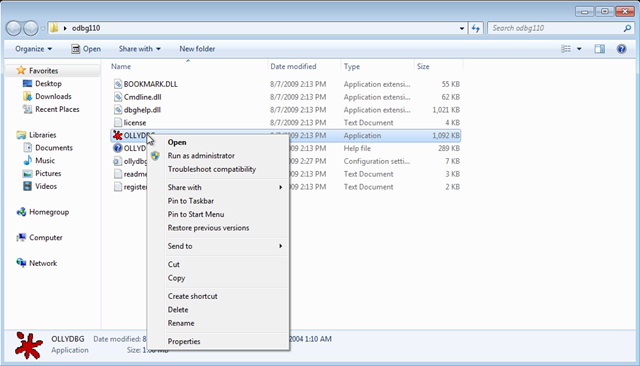
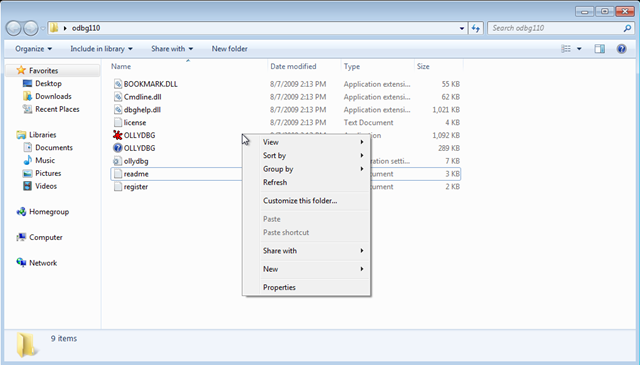
Windows 7 UI glitch
0 commentsWhile reading this post I’ve remembered a quirk of the Windows 7 UI which annoys me to no end: you have to click on a non-empty part of the list to get the item-specific menu, otherwise you will get the folder-specific menu, as shown in the second screenshot:
This is in fact consistent with the way the Windows XP UI works, with a small, but important, difference: under Windows XP you do not get the impression that the whole row is selected (and, in consequence, it should work the same), while under Windows 7 you do.
Win 7 is a big step forward (do not run Vista! do not run Vista!), but it still has its glitches (the glowing-animating progress bar is pretty annoying also).
delicious/cdman83
0 comments| Posted: 06 Aug 2009 02:22 AM PDT |
| Posted: 05 Aug 2009 11:16 PM PDT |
| AV-Test.org · Tests of Anti-Virus- and Security-Software Posted: 31 Jul 2009 01:30 AM PDT Interesting, freely available (with comparison) statistics from AV-Tests about the frequency of AV updates. |
| Canonical Blog » Blog Archive » Launchpad is now open source Posted: 01 Aug 2009 01:26 AM PDT Launchpad is opensource under the AGPL :-) Nice move and an interesting (but logical) choice of license. Via http://taint.org/2009/07/21/220502a.html |
| glTail.rb - realtime logfile visualization Posted: 01 Aug 2009 01:25 AM PDT |
| Posted: 31 Jul 2009 11:49 PM PDT Good list for sysadmins about (free) external resources they can use to monitor their IP space: ISP FBL's like the one from RoadRunner: http://feedback.postmaster.rr.com/ SenderBase: http://www.senderbase.org/ TrustedSource: http://www.trustedsource.org/en/feedback/checking |
| Posted: 03 Aug 2009 11:21 AM PDT |
| Posted: 03 Aug 2009 10:20 AM PDT |
| Code Complete 2nd Edition - Code Complete 2 Home Page Posted: 03 Aug 2009 10:20 AM PDT |
| Ship it! A Practical Guide to Successful Software Projects Posted: 03 Aug 2009 10:19 AM PDT |
| open video codecs discussion at Mozilla at hacks.mozilla.org Posted: 03 Aug 2009 04:14 AM PDT Very good panel discussion about ogg theora, its history and the issues surrounding it. |
| Posted: 03 Aug 2009 02:12 AM PDT |
| Posted: 03 Aug 2009 12:10 AM PDT If you think you understand NULLs in RDBMS's, read this. My head is hurting now and I feel a distinct urge never to use NULLs :-). Or at least find a good book to read about the theory. |
| as days pass by, by Stuart Langridge — On tolerance Posted: 04 Aug 2009 07:09 AM PDT "With regard to the freedoms that stem from the software being open source, something like Ubuntu isn't just, say, ten times better than Windows or Mac OS X, it is infinitely better. Sometimes I forget that just because my stuff's infinitely better, it doesn't mean that I can divide by that infinity to conclude that their stuff's worth zero, and it certainly doesn't mean that they think it's worth zero" |
| Posted: 04 Aug 2009 07:08 AM PDT A very useful tool for sending signals to the JVM under Windows (under Linux you can just do kill -3 1234). Fount id via Stackoverflow: http://stackoverflow.com/questions/912889/how-to-send-interrupt-key-sequence-to-a-java-process |
| YouTube - Hacking the Defcon 2009 badge Posted: 05 Aug 2009 02:45 AM PDT |
| Posted: 05 Aug 2009 02:13 AM PDT |
| rnicrosoft.net - The home of Nick Harbour's tools and techniques Posted: 05 Aug 2009 12:19 AM PDT |