 Disclaimer: I never worked as a professional network admin and all my experience was gathered in small testing environments. Also, I received a 12 month evaluation key from GFI for the purpose of writing this review, however aside from the key, I didn’t receive any form of compensation from anyone for writing this review.
Disclaimer: I never worked as a professional network admin and all my experience was gathered in small testing environments. Also, I received a 12 month evaluation key from GFI for the purpose of writing this review, however aside from the key, I didn’t receive any form of compensation from anyone for writing this review.
As we all know, security is a process, which means that we need metrics and tools to monitor the values of the metrics to have an acceptable amount of security. GFI LanGuard is a tool which is designed to do just that: scan your network periodically and report the “security status” of each network node.
The installation went smoothly and the interface is quite intuitive. (This despite the fact that I used Windows 7 which isn’t officially supported – only Windows Vista is – which further proves that application compatibility between Vista is 7 is very good).
The good:
- Easy to use interface
- When problems appear, a clear indicator is shown, together with an easy fix (along the lines of: “Foo is wrong. Click here to fix it”)
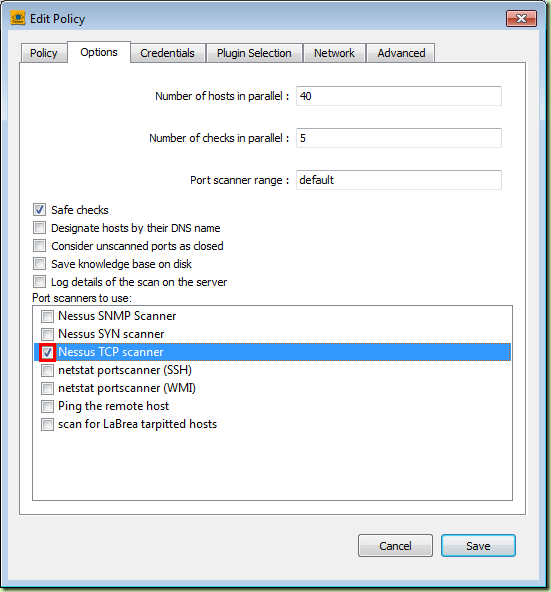
- There are multiple options for customizing workings of the software
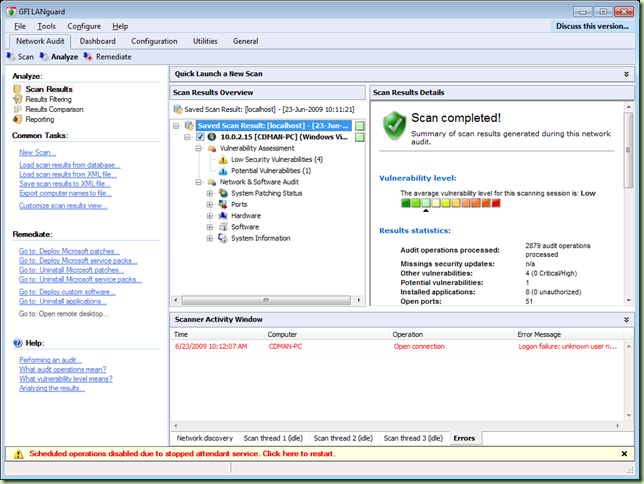
- The results are displayed and summarized in an easy to understand way and older reports can be retrieved fast (this is a very nice default compared with Nessus – and many other tools for that matter, where you have to explicitly save your reports)
- There are many “common sense” checks done which are not directly related to exploits / patches. For example things like “user X has never logged in, please consider removing it”.
- The scanning is “agent-less”. This is very nice for many reasons (security – you don’t have to wait for the agent to download, compatibility – the problems with the agent being incompatible with HIPS/AV products is eliminated, etc)
- The scans are multi-threaded. The number of threads seems to be fixed at 3, however this seems to be a good value (although on an extra-beefy machine – think dual quadcore – you might want to use higher values)
- The link to the forum (“Discuss this version...” in the upper right corner) – communities are very useful in resolving problems and can create a safety net for low priority support issues
The bad (to be clear: this is a fine product. the following list is more along the lines of “good to know” stuff – also, it is human nature to observe more things which are wrong, rather than things which are right).
- The scheduling service kept getting stopped with the warning: “Scheduled operations disable due to stopped attendant service”. Given that I didn’t test the scheduled operations this wasn’t a big problem. Also, I was testing on Windows 7, which is officially not supported by GFI LanGuard at this moment.
- Locally (on Windows 7, so it might just be that not all the kinks has been worked out) it found some spurious open UDP ports (spurious because I couldn’t reproduce it) related to “trojans”
- The list of installed software (in the “inventory” part) seems to take only the list of installed software from the registry (ie. things which you see in “Add/Remove programs”). This can be easily circumvented by using any package from Portable Apps for example. Of course scanning the entire harddrive would be be much more time consuming
- The documentation recommends disabling firewalls and AV products during scanning :-(. And it really does matter. Scanning a remote XP system with the firewall took around 7 minutes, while scanning it without the firewall took 2 minutes. The same system got scanned by NMAP in ~1.5 minutes (firewalled, and it identified correctly all the open ports – with the mention that I disabled pinging, because it would have assumed that the host is down). To be fair, NMAP doesn’t do exploit testing on the discovered ports. An other positive part: Nessus was slower than GFI LanGuard – it took 7 minutes to scan the non-firewalled XP machine (note: you need to disable the Nessus SNMP port-scanner for this to work – otherwise it seems to conclude that there are no (!!!) open ports on the remote machine – a nice way to trick Nessus?). Also, it found much fewer problems and the interface is not as friendly (disclaimer: I’m not a Nessus expert and it was using the free home feed). Even though the performance difference is large, there is no easy way to deactivate/activate (or add exceptions) to firewalls on remote systems, which means that the whole process (of turning firewalls on/off) can be rather error prone.
- Some input fields don’t do input validation, it is not entirely clear in what format they expect the input and the feedback that the input was incorrect is given relatively late. Concrete example: When creating a new scan I accidentally typed the username in the format “\\foo\bar” instead of “foo\bar” (I was copy/pasting, can you tell :-)). The feedback came only after the scan ended, in the error log.
- Speaking of the error log, there seems to be no visual differentiation between the log entries associated with different scanning runs and I found no way to clear the error log.
- The checks are mainly geared towards Microsoft products. While Microsoft is a big target, attacks against third-party applications are becoming more common (for example the Adobe products seem to be a big target these days). For similar checks in the free category we have the Microsoft Baseline Security Analyzer. To find outdated versions of software (not just MS software) you should consider the CSI/PSI products from Secunia (the PSI version being free). Be cautious though, the CSI/PSI product does not do configuration validation (either for Microsoft of third-party products)
- GFI LanGuard doesn’t seem to do service detection. For example if I run my webserver on port 80, it gets correctly identified as a webserver and the relevant checks are performed (for example PHP is detected). However if I change the port 12345, it simply gets flagget as the Netbus trojan. This reliance on default port numbers rather than protocol detection can create both false-positive (like a webserver running on port 12345) and false negative (an attack tool running on port 443) issues.
All in all it is a good general tool. It lacks certain capabilities of more specialized tools, but the utility of presenting all the information in one unified interface should not be underestimated. The pricing is per scanned IP / year, which is pretty much the standard for these types of tools. My conclusion is that if you have some budget for such products, GFI LanGuard is a good option. If you have no budget at all, you might want to consider some of the free products listed in the review (then again, the free products are not as well integrated, so in the end they might end up costing you more...) And finally if you have a larger budget, you should consider going with a “best of breed” solution (even though there might be an overlap between the features of the respective tools, it is good to have multiple validation of the same problem area (just in case a tool misses some of them).
Picture taken from kat m research's photostream with permission.